Privileged Access Management solution offers additional security to privileged accounts.
What is Privileged Access Management (PAM)?
PAM accounts are special accounts that function as superusers or administrators. Privileged accounts have access to more capabilities than regular users. Protection and management of privileged access accounts is critical since any kind of security or data breach will compromise the security of the whole ecosystem. And so, accounts that have information about every other user account and other exclusive access need more layers of security. All the above-mentioned issues can be efficiently resolved through a PAM solution, in the form of additional security known as a Privileged Access Management Solution.
How PAM helps to avoid Cyber Threats
Limit Privilege
Limiting the access of applications, technology, and people, to privileged users automatically ensures that any traces of wrongful entrances are also diminished.
Protect against Data Breach
It minimizes the number of rights for every privileged account and so if that account gets compromised it will be within a very narrow scope of a data breach.
Protect credentials
Protects credentials of confidential software, accounts, privileged accounts, and other related systems. All this is managed in a secure repository.
Automatic Sync
After updating a user in miniOrange, it will automatically get updated in all the integrated directories/applications.
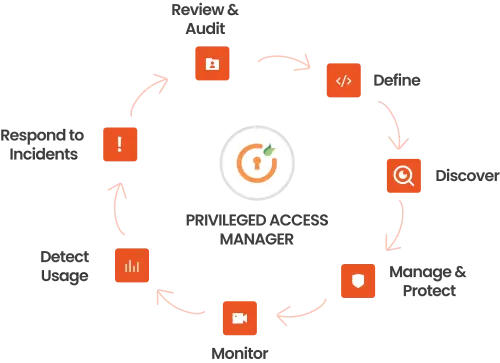
Understanding PAM – Privileged Access Management
Privileged accounts can pose a considerable risk to an organization’s security if they get compromised; hence, privileged access management becomes indispensable. Let us take a scenario where the credentials of a normal user account get compromised. The hacker will have access to information and access rights of that particular account only. On the other hand, if any privileged account gets compromised, the hacker will have far more comprehensive access to details of not just one user but information access on many levels and of several accounts.
Due to the sensitive nature and rights of privileged accounts, cyber criminals target them, which further enables them to successfully compromise the security of the whole organization. According to research by Forrester, nearly 80 percent of data breaches involve privileged accounts getting targeted. This is where Privileged Access Management – PAM plays an indispensable role by providing granularity as it helps an organization to have full control and management over the activities happening in their ecosystem.
How miniOrange seamlessly integrates with PAM solutions to secure your sensitive data and secure your accounts
Endpoint Privilege Management
The increasing number of endpoints and the growing complexity of cyber threats are making organizations more vulnerable than ever, and that’s why effective endpoint privilege management is essential to protect sensitive data, prevent unauthorized access, and mitigate the risk of security breaches. The Endpoint Privilege Management feature of miniOrange’s Privileged Access Management product enables you to remove local admin rights, enforce the least privilege and deploy endpoint security controls.
Agentless PAM
The Agentless Privilege Access Management feature offers a hassle-free deployment process, as it eliminates the need for installing and managing PAM agents on each endpoint. This not only simplifies the deployment, but also saves valuable time and resources. Moreover, organizations can mitigate the risks associated with agent vulnerabilities or compromise by removing the dependency on PAM agents, ensuring a more secure privileged access management environment.
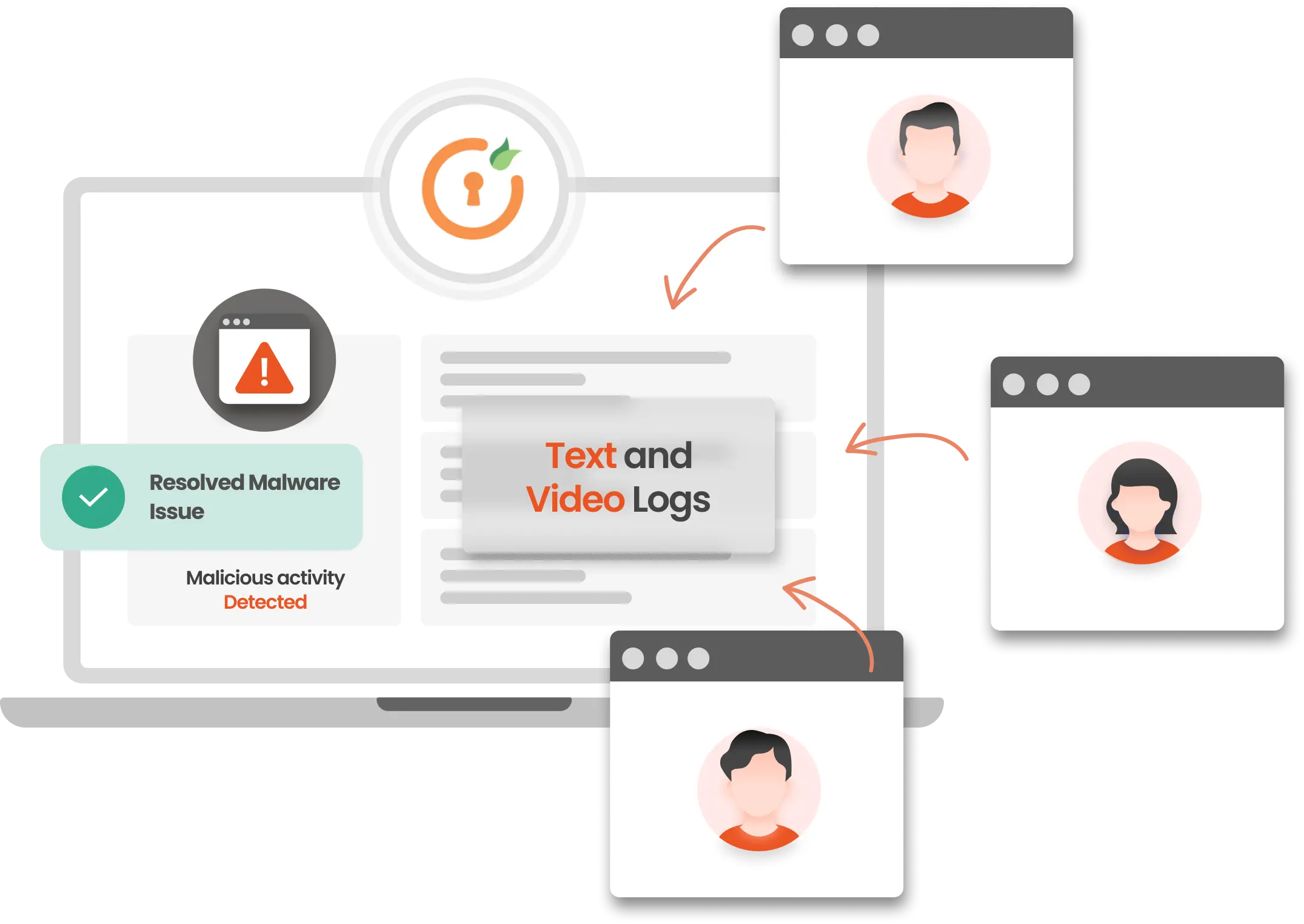
Password Vault
Protect your user accounts in a centralized manner with the Password Vault feature of miniOrange’s Privileged Access Management product. Password Vault Identifies and adds privileged accounts to the management system, and ensures the secure storage of privileged passwords in an encrypted vault while effectively eliminating embedded credentials in scripts and code. It also auto-updates passwords periodically. This eliminates the risk of credential theft of privileged accounts and ultimately improves endpoint security.
Just in Time Access
When certain users or employees require urgent access to resources that are restricted to them, then with Just in Time Access you can enable them with appropriate privileges when necessary and for the least amount of time so that both work & security doesn’t get hampered. This feature ensures that security doesn’t bring down convenience, and both security & convenience are balanced out properly in order to provide a secure and efficient work environment.
Session Monitor & Control
Get real-time visibility through live session streaming, enabling you to monitor and respond to potential security threats promptly. Session recording ensures a comprehensive audit trail for compliance and forensic investigations. You can Instantly terminate sessions to halt suspicious activities and minimize the impact of security breaches. Also, you and your team can get instant alerts when unauthorized behavior is detected, and you can easily monitor and analyze session activities with an intuitive dashboard.
Privilege Elevation & Delegation
With Privilege Elevation & Delegation, you can grant specific users with time-limited access to resources that are restricted to them as per their current privileges. Instead of giving standard users permanent access to critical resources, you can easily give them exclusive time-bound access to minimize the risks associated with overprivileged users. You can ensure maximum security while saving time by following the principle of the least privilege.