Ransomware is no longer a threat only to private companies, endangering their operations, revenues, and profits. Today, ransomware threatens national security and has become a global crisis that potentially affects every one of us.
These three examples show the seriousness of the ransomware situation:
- The ransomware attack on JBS, the world’s largest meat processing company, resulted in immediate concerns about a shortage of beef and pork and an increase in prices. Because of the attack, JBS had to shut down plants in the United States, Canada, and Australia.
- Colonial Pipeline, the largest pipeline operator in the United States, was also hit by a ransomware attack. Colonial provides roughly 45% of the East Coast’s fuel, including gasoline, diesel, home heating oil, jet fuel, and military supplies. As a result, gasoline demand immediately rose, causing shortages, panic buying, and price increases.
- National Health Service hospitals in the United Kingdom were hit by ransomware, disabling their services and forcing them to move patients to other facilities for treatment. In total,16 hospitals were shut down. Also, multiple attacks against U.S. hospitals have been carried out in recent months, suspending some surgeries, delaying medical care, and costing millions of dollars. Equally concerning are reports of ransomware attacks on medical institutions working on vaccines or treatments for COVID-19.
These attacks should serve as a wake-up call to all of us. But they are just the most obvious cases. Here are more reasons for alarm.
- Industry analyst firm Gartner reported recently that the number of different ransomware types has grown by more than 700% since 2016.
- Datto, a provider of cloud-based software and security solutions, asserts that up to 35% of attacks are resolved only through paid ransoms.
All this evidence demonstrates that ransomware is now a public threat that can affect all our lives. We need to ask ourselves what we can do better and faster to mitigate these risks at minimum costs.
Battling ransomware with CryptoTrap
Imagine you’re conducting a major battle against a well-equipped and clever assailant. Now consider the huge advantage you could gain by obtaining not only intelligence about when and where an attack will happen, but also troops on the ground to give you breathing room to remediate the risk and mobilize your own army to completely defeat the enemy.
That’s what CryptoTrap does.
CryptoTrap from TrapX is specifically designed to defeat ransomware attacks. Since its initial release as a standalone server, it has been improved and integrated into DeceptionGrid, our flagship product, as an optional component of a DeceptionGrid full OS high-interaction trap.
DeceptionGrid has a proven record of ransomware activity detection and is already deployed at hundreds of enterprises, including Fortune 500 companies, in more than 50 countries. CryptoTrap can be added to DeceptionGrid in seconds to provide immediate detection and threat isolation of any ransomware activity in your network.
How it works
To attract attackers, the CryptoTrap deceptive shared folder is mapped on an organization’s endpoints in addition to its local drive. When the CryptoTrap deceptive server is attacked, it keeps the threat actors very busy by automatically and continuously populating the shared folder with fake documents and many types of files to encrypt or steal. This activity slows down the attack. Once these documents and files are in the process of being encrypted or stolen, you immediately receive an alert identifying the source of the attack (location and timing). Through integration with your security system, CryptoTrap triggers remediation of the threat source via automatic or manual isolation.
This screen capture shows an example of an alert generated in real-time when ransomware activity is detected by a CryptoTrap server.
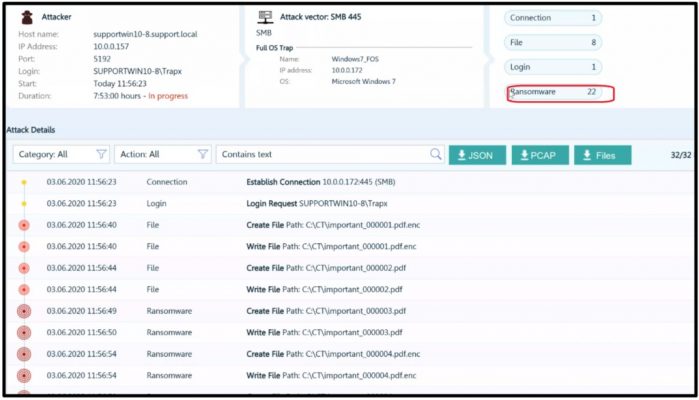
DeceptionGrid also allows you to save deceptive files in the CryptoTrap shared folder. Once they are opened or stolen, the tool transmits the attackers’ public IP address, enabling security teams to identify them.
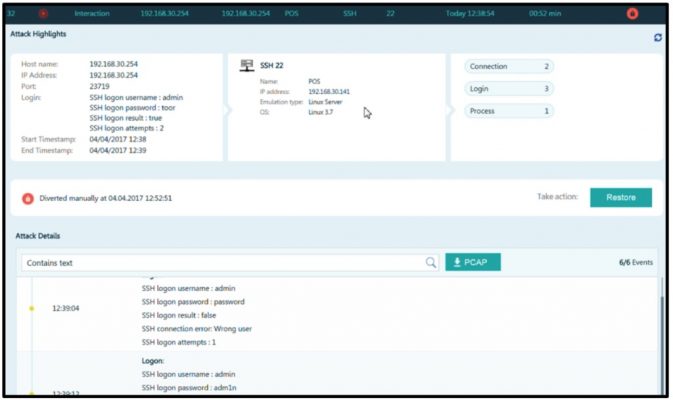
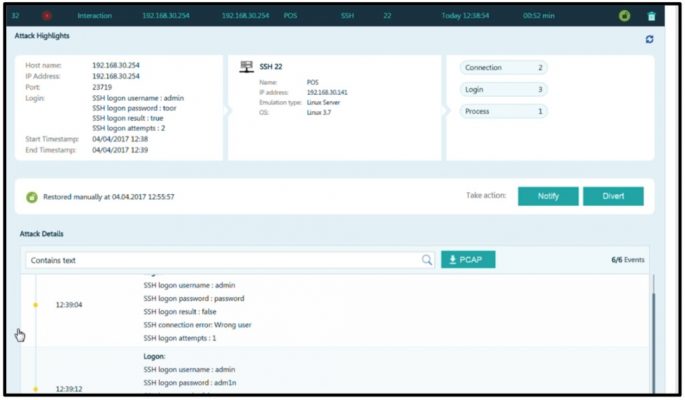
DeceptionGrid can be integrated with your NAC system to automatically or manually divert and restore attackers’ source endpoints.
Here is an example of manual diversion, followed by restoration of an endpoint after cleaning it to remove the ransomware infection.
Deception at work for good
As I worked with partners and customers over the years, I was always impressed by the power of DeceptionGrid with integrated CryptoTrap to detect and defeating ransomware attacks. TrapX takes pride in helping organizations to secure their resources against ransomware – and ultimately turn the tide in this ever-expanding crisis.
About TrapX Security
TrapX has created a new generation of Deception technology that provides real-time breach detection and prevention. Our proven solutions immerse real IT assets in a virtual minefield of traps that misinform and misdirect would-be attackers, alerting SOC teams to malicious activity with immediate, actionable intelligence. Our solutions enable our customers to rapidly isolate, fingerprint, and disable new Zero-Day attacks and APTs in real-time. TrapX Security has thousands of government and Global 2000 users around the world, servicing customers in manufacturing, defense, healthcare, finance, energy, consumer products, and other key industries.
For more information, contact us at contact@smartnet.net.vn
