
VEDR solution with very useful features, helps IT directors, SOC and MSSP (Managed Security Service Provider) to fully control endpoints in the information system as follows:
– VEDR collects data (Data Collection) on endpoints in a detailed, non-redundant, and highly reliable manner. This data helps monitor all activities at endpoints, and can save up to 70% of IR (Incident Response) and DF (Digital Forensics) costs when incidents occur.
– VEDR can detect the most sophisticated attacks using a platform of algorithmic chains, machine learning or rule-based, analyze collected data and issue warnings about signs of intrusion.
– VEDR has an investigation system with fast and accurate search and comparison of security information, on large data blocks collected from endpoints, to serve IR and DF work.
– VEDR has diverse response capabilities , can isolate from IT systems, suspend or stop malicious endpoints, users, processes, files, and network connections at any time.
VEDR has two components: Server and Client Sensor. The server has two options. The first is to install internally (On-premise) in the customer\’s IT system, for customers who do not want data to be taken outside the IT system. The second is to use Veramine\’s cloud server, for customers who do not want the cost of internal servers and trust cloud technology. Both options can be deployed very easily.
Servers also use big data technology to calculate and store information, allowing horizontal scalability: more workstations can be served by installing more servers.
The Veramine Platform efficiently collects all security-related events through intelligent sensors, and sends them to Veramine’s cloud-based servers or to customers’ own servers. The server uses advanced machine learning and machine learning algorithms to detect attacks such as Mimikatz password harvesting, kernel-mode exploits, local elevation of privilege (EOP), process injection, unauthorized access, and other attacks. The server displays these events both in raw form and via an intuitive web interface that allows customers to easily search all collected data for more efficient incident handling and proactive investigation. A security analyst who notices unusual behavior can easily terminate or suspend an individual process, isolate a process or computer from the network, terminate or disable a user account, or prevent a program from executing. The sensor also supports memory forensics by uploading the memory contents of a specific process or an entire computer to a server.
1, Data collection
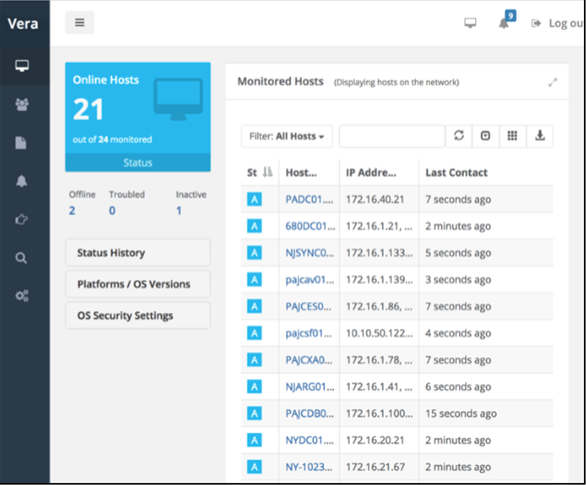
The strength of any EDR product depends on the scope and fidelity of its ability to observe and display machine behavior. The Veramine sensor uses both user-level and kernel-level components to securely and reliably collect and process security-relevant system events. Veramine uses a variety of techniques to minimize the negative impact on system stability and prevent other security products from misidentifying the Veramine sensor as malware. The Windows sensor is built by former Microsoft kernel-level programmers and engineers who have spent more than 20 years tuning, developing, and securing programs running in the Windows kernel. The sensor is continuously optimized for performance and efficiency to minimize resource usage at the endpoint. After a brief initial run, the sensor consumes less than 1% of CPU. Running the sensor on the weakest cloud VMs (Azure A0 or AWS t2.nano) has a negligible impact on the overall performance of the machine.
Veramine collects data that is rich, detailed, and suitable for alerting and investigation while maintaining a small data transmission volume. All data relevant to system safety is collected as follows:
+ Process: create, open, inject, remote access, create new remote thread, load image, command argument
+ Registry: key access, value operation
+ System security: security tokens and flags, privileges, file security, binary policy violations, service tracking
+ Network: protocols including TCP and UDP, connections and ports, DNS cache monitoring, URL access
+ User: logins, privileges, console usage, remote, or local
+ SMB: session and file access
+ Binaries: all program files (binaries) loaded for execution
- Data is collected continuously in real time.
Continuously collecting such an extensive range of end-to-end behavioral events, if done in a simple and unsophisticated manner, would exhaust both the client and server resources of a typical EDR solution. Veramine has developed the ability to efficiently collect these events and intelligently select the necessary information to send from the sensor to the server. All relevant or necessary details are sent by the sensors to the server in full. As well as limiting unnecessary information, the sensors require very little network traffic. A normal client may send only a few hundred kilobytes of events per day while a high-event client may send as little as 100mb per day. When the client loses connection to the server, the events are stored and wait until they can be sent to the server.
The Veramine sensor is easy to deploy and manage. Each Veramine user is provided with a pre-configured installation. With the information included in the installation file, the user can simply install the sensor as an administrator on any computer and it will start sending events – no configuration required! The sensor is built to prevent accidental or intentional removal by the system. The sensor is easy to stop, start, restart or uninstall from the web portal interface.
2, Automatic detection of threats
Sensor data streams are continuously analyzed by the Veramine server using a variety of rules-based and machine learning algorithms to identify unusual or suspicious behavior. Comprehensive visibility and visibility into security-relevant endpoint behavior enables the server-side detection engine to uncover a wide range of cybersecurity threats, including complex attacks that are difficult to detect, such as in-memory, fileless attacks.
The power of the algorithms is constantly being enhanced and updated. Veramine aims to have the most comprehensive ability to detect and warn of the tactical strategies and attack techniques listed in the Mitre matrix.
Intrusion detection is also supported by Veramine’s machine learning platform, which is designed to be scalable, upgradable, and interoperable. It uses big data technology to evaluate sensor data streams and can integrate all machine learning techniques written in different languages to handle any data problem, while providing different learning supervision. For example, the following 3 types of detection are built on different chains of machine learning algorithms:
+ Process performance profile: tracks historical metrics for each process by process name and alerts on divergence from established norms.
+ Data theft: track network usage history of each process by name and warn about divergence.
+ User tracking: track login behavior patterns for each user and alert on anomalies.
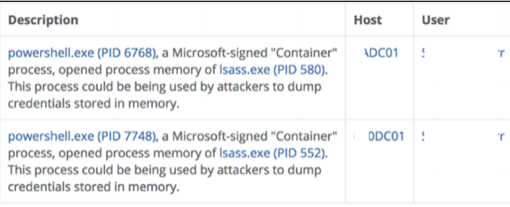
The following figure shows a Veramine detection sample resulting from an attacker stealing security certificates on a customer’s computer using the Powershell Invoke tool – Mimikatz. The Veramine detection tool observed the Powershell.exe process opening the memory of the lsass.exe process, one of the most accurate indicators of password extraction behavior. The detection results include all the information needed to investigate the situation – the suspicious process (powershell.exe), the process that was opened (lsass.exe), the computer on which the process was running, and the user who executed the suspicious process. The detail pages are linked to the process and show all loaded modules, any network connections, the parent process, any child processes, etc.
3, Easy investigation and search for attack information
The sensor data stream is certainly useful for detection. However, the collected information is also presented on the client’s web interface, with useful information distilled, connected, and supplemented. This web interface allows users to perform specialized searches to find answers that facilitate and empower investigations and intrusion response, and also enables effective threat hunting.
To investigate the detection of malicious Powershell.exe, we start with the process details page to see the entire process tree, including any child processes that were triggered by the malicious powershell.exe. The following figure shows this view.
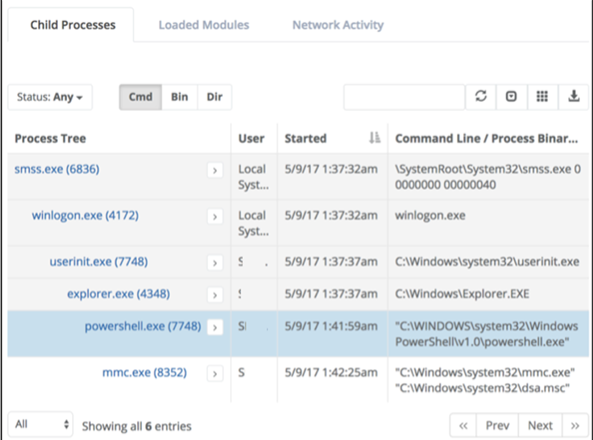
Clicking on the supervisor link of the parent process explorer.exe (PID 4348) will show other peer processes for the malicious powershell.exe (PID 7748) process, processes launched by the same parent. It is just a few clicks in Veramine\’s Process Finder interface to find activities related to the process, such as the following:
+ All processes launched in machines on the system using the same compromised user account
+ All processes are launched at the same time on the same computers as the malicious Powershell.
+ All child processes of PowerShell.exe are launched on the same user\’s computers at any time.
4, Response
The Veramine platform provides monitoring and response features to enable fast and effective incident response from a central console. Monitors and analysts can send response actions to Veramine sensors to interact with processes, executables, users, and computers.
The following process-related response actions are currently available:
+ Pause or terminate any running process.
+ Create and upload the process\’s memory contents to the Veramine server.
+ Prevent a process from making any outgoing network connections
In addition to these individual processing commands, the Veramine sensor supports in-memory search capabilities via Yara rules.
Veramine Sensor provides actions with run file:
+ Prevent an executable file from being loaded by any process.
+ After loading an executable file, prevent the loaded process from connecting to the network.
+ The Veramine platform also retains a copy of each executable file loaded by any process and makes that file available for download from the Veramine web interface.
The Veramine sensor also provides some user-related actions. It can disable or enable a local user account or disconnect a specific user\’s RDP login session.
Veramine Sensor provides computer related actions:
+ Turn off the power, Restart, or put the device to sleep.
+ Prevent the server from making network connections to destinations other than the server.
+ Uninstall sensor.
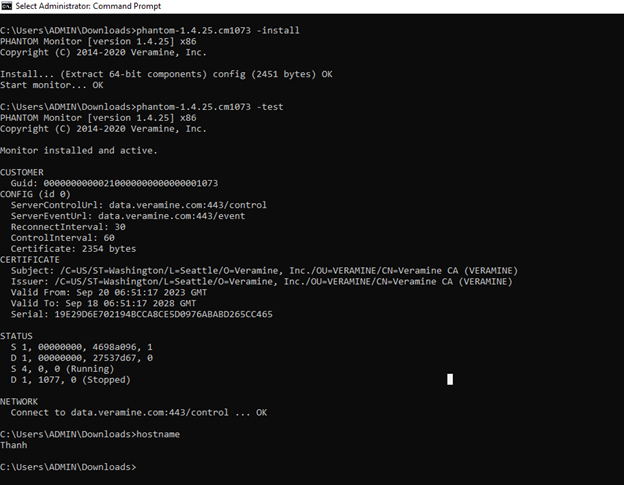
+ The Uninstall Sensor action is specifically mentioned because the web portal is the only way to uninstall the product sensor. The Veramine sensor trial version can be easily uninstalled using the command line.
For infected Binary: Isolate binary on entire network, block, scan with virus total.
5, Trap system
Veramine has the ability to place traps anywhere on the system, on physical workstations or virtual machines. These traps monitor the intruder\’s activity, and limit the intruder\’s capabilities. Traps can spoof programs, processes, users, credentials/passwords, drivers, binaries, mutexes.
For more information about VEDR, please contact contact@smartnet.net.vn





