Traditional EDR solutions focus only on endpoint activity to detect attacks. As a result, they lack the full context to analyze attacks. This leads to an incomplete picture and a high rate of false positives, requiring organizations to use multiple point solutions and large incidence response teams.

Qualys brings a new multi-vector approach and the unifying power of its highly scalable cloud platform to EDR, providing vital context and comprehensive visibility into the entire attack chain.
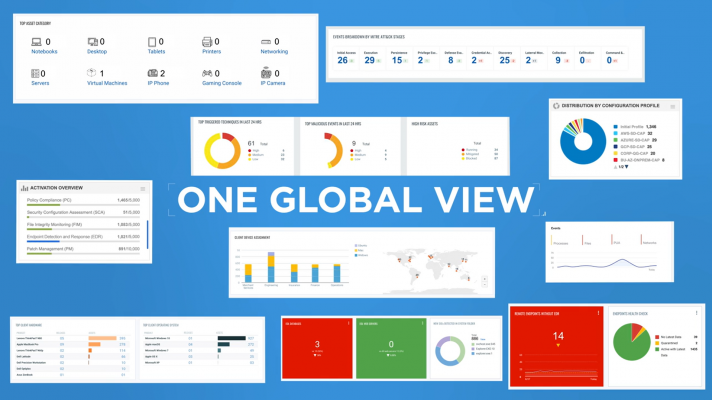
With this new approach, Qualys multi-vector EDR dramatically reduces the number of false positives by unifying different context vectors like asset discovery, rich normalized software, inventory endoflife visibility, vulnerabilities and exploits misconfigurations, indepth endpoint telemetry and network reachability. With a powerful back end to correlate it, all for accurate assessment, detection and response all in a single cloud-based app.
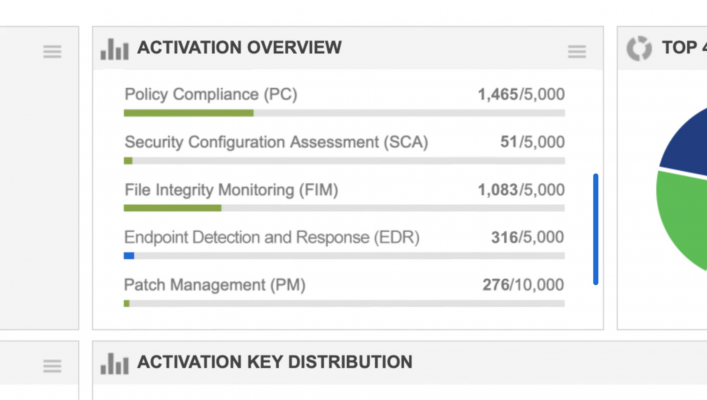
The app is powered by lightweight cloud agents that continuously collect and stream data to the Qualys Cloud platform, where the information is correlated, enriched and prioritized for real time visibility into everything that’s happening on the endpoint and the surrounding network.
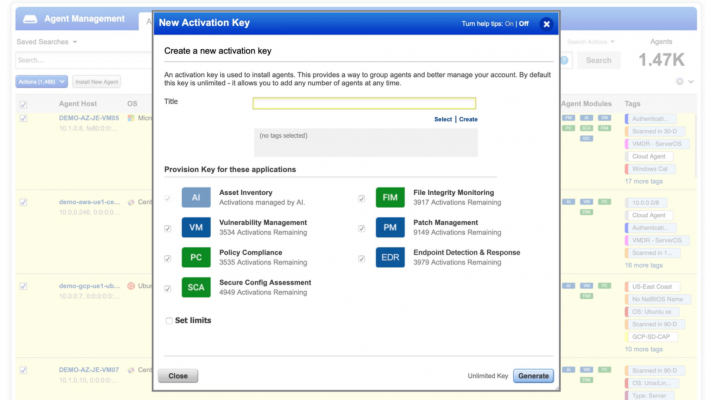
With Qualys, you only need one agent to perform critical security functions like Asset inventory, Vulnerability management, Configuration management, File integrity monitoring, Patch management, and now EDR, eliminating multiple agents, reducing complexity and lowering costs. Qualys Multi – Vector EDR leverages the Qualys Cloud platform to collect and correlate vast amounts of It security and compliance data, giving threat hunters and security analysts unprecedented context and real time insight into the endpoint to carry out speedy threat hunting and response.

It also provides comprehensive response capabilities that go beyond traditional EDR options like Killing process and Network connections, Quarantining files, and much more. And it uniquely orchestrates responses such as preventing future attacks by Patching software, fixing misconfigurations, and uninstalling software before endpoints are compromised.
