Since the launch of THOR Cloud Lite in September, our team has been dedicated to developing a more powerful version of THOR Cloud that incorporates the full scanner with its extensive suite of forensic modules and expansive detection signature database. Today, we are excited to announce the general availability of THOR Cloud, which offers a streamlined method for conducting automated compromise assessments on your endpoints.
Like its predecessor, THOR Cloud does not require the installation of agents on the endpoint or the deployment of servers or services within your network. Setting up is straightforward: create an account, and you can start scanning immediately. The platform is designed for ease of use with an intuitive interface that allows new users to get started in minutes—no need for navigating through Windows command lines, and no extensive training or user manuals necessary.
After a scan is completed, the launcher automatically cleans up by removing itself along with the downloaded scanner, ensuring that nothing resides on the local hard drive. Additionally, reports can be encrypted with your public RSA key, providing robust end-to-end encryption for maximum security. Whether it’s for targeted compromise assessments, speeding up forensic analysis, or enabling your SOC team to verify alerts from your EDR, THOR Cloud offers a lightweight, efficient, and highly effective solution focused on detecting and analyzing hacking activities.


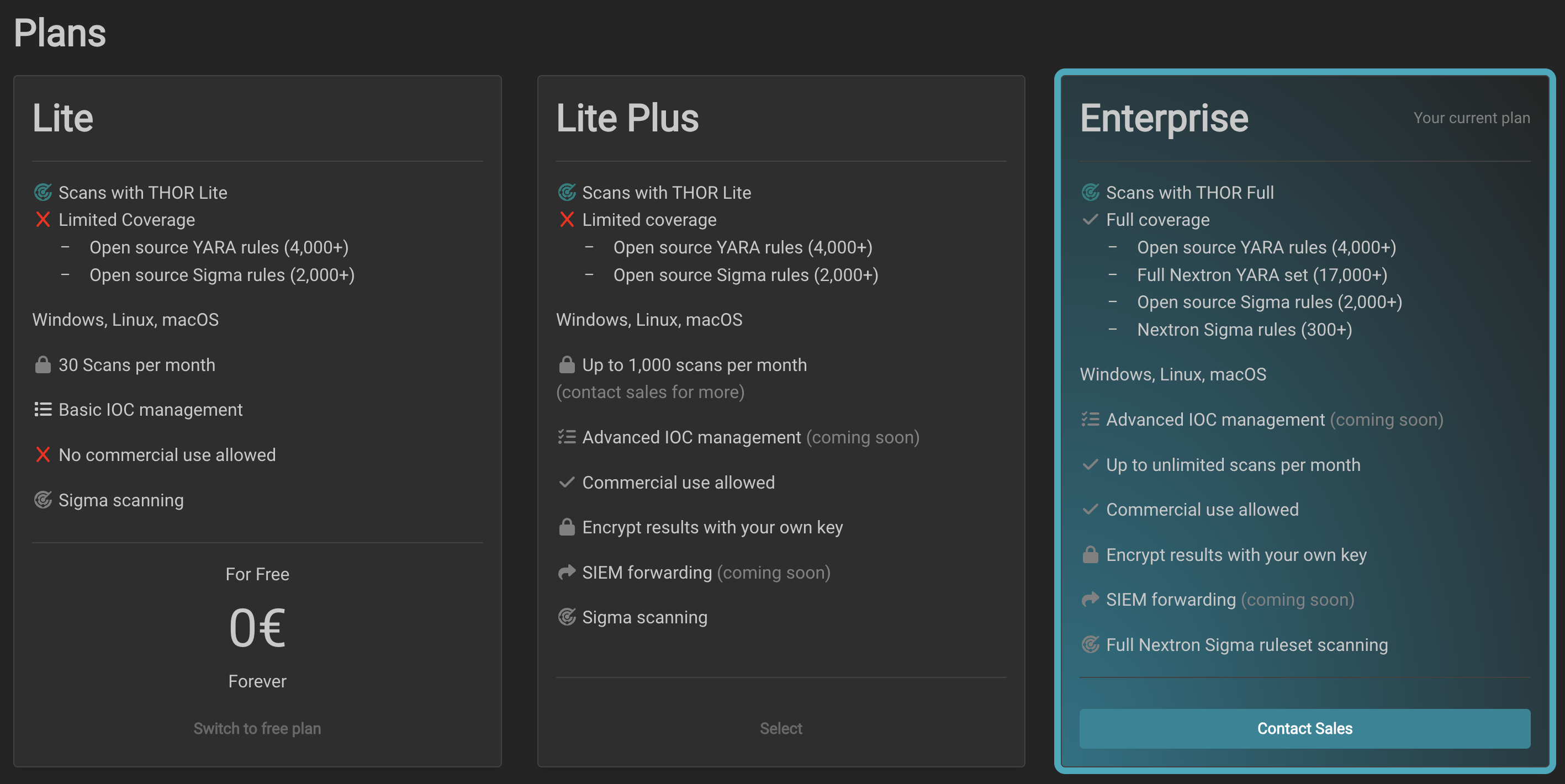
Key Differences Between THOR Cloud and THOR Cloud Lite
THOR Cloud is engineered for enterprises and professional services that demand deep, comprehensive forensic capabilities with extensive coverage. It provides a complete suite of forensic modules and access to a broad database of over 32,000 detection rules for detailed security assessments.
Conversely, THOR Cloud Lite is better suited for individuals, non-profits, and organizations that maintain their own set of detection rules and require very targeted and specific scans for a narrow range of threats. This makes it ideal for users who perform specialized, less comprehensive security checks.
Expanded Scanning Capabilities
THOR Cloud:
- Equipped with the full version of the THOR scanner, including all 31 forensic modules.
- Utilizes a vast signature database with over 30,000 YARA rules, 2,000 Sigma rules, and thousands of IOCs, ensuring thorough detection and analysis of security threats.
THOR Cloud Lite:
- Operates with a basic version, THOR Lite, featuring a limited set of open-source YARA rules and IOCs.
Licensing and Usage Flexibility
THOR Cloud:
- Provides a scan- and host-based licensing model that supports unlimited scans on specified endpoints within a subscription period, ideal for enterprises needing extensive, regular scanning.
- Allows commercial use for service providers.
THOR Cloud Lite:
- Offers only a scan-based licensing model, which is suitable for organizations with infrequent scanning needs.
- Restricted to non-commercial use, primarily intended for educational or personal exploration.
Data Retention and Security
THOR Cloud:
- Supports storing encrypted scan reports for up to one year, aiding in compliance and long-term security analysis.
THOR Cloud Lite:
- Retains reports for up to three months, suitable for less stringent retention needs.
- Does not support encrypted reports, which may limit its use in environments requiring high data confidentiality.
Highlights
Nextron’s Private Signature Set
THOR Cloud leverages Nextron’s full private signature set, encompassing more than 32,000 detection rules, to provide comprehensive threat identification capabilities. This extensive set includes a wide array of generic and highly effective detection rules designed to identify a diverse range of hacking-related threats. From backdoors and web shells to hack tools and their outputs, the signature set is adept at detecting malicious activities and system anomalies.

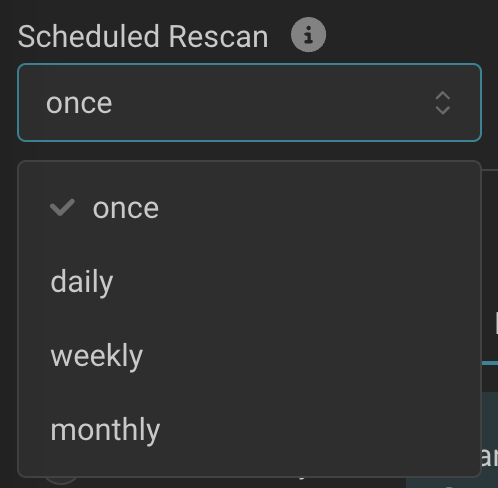
Scheduled Rescans
THOR Cloud simplifies ongoing security assessments through its Scheduled Rescans feature, which automatically sets up and manages scheduled tasks or cron jobs on target systems. Users can easily configure multiple campaigns with different frequencies—such as daily quick scans and weekly full scans—directly from the campaign configuration menu.
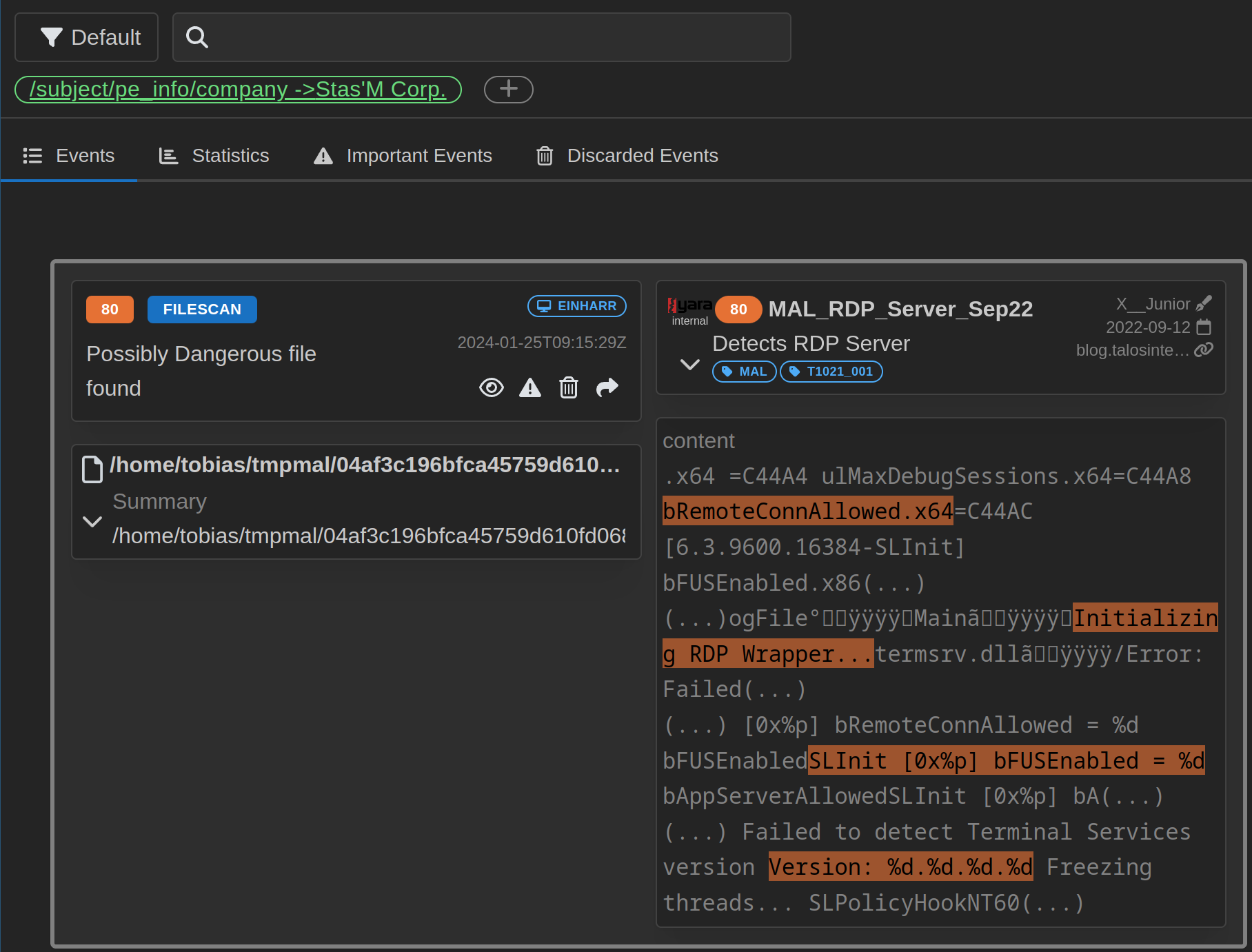
New HTML Report (coming in Q4/2024)
THOR Cloud’s latest update introduces enhanced HTML reports, designed to improve readability and interactivity for a streamlined user experience. These reports leverage the sophisticated JSON output of the forthcoming THOR v11, set for a TechPreview in Q4/2024, ensuring detailed and actionable security insights.
Key features include optimized UX for better navigation, interactive elements such as report-based and global filter management, which allow users to apply filters across various reports within a campaign. Important aspects of findings are automatically highlighted, drawing immediate focus to critical data points.
Additionally, the integration of ChatGPT introduces conversational AI capabilities, enabling dynamic interactions with report data for deeper analytical insights. This suite of enhancements transforms the HTML reports into a more interactive and user-centric tool, facilitating efficient threat assessment and management.
Planned Upgrades and Features in THOR Cloud
THOR Cloud is preparing to implement several enhancements aimed at extending its capabilities and refining the user experience. These updates focus on technical improvements and functionality expansions:
Enhanced HTML Reports: Pending the deployment of THOR v11 and its refined JSON output, THOR Cloud plans to introduce upgraded HTML reports. These reports will incorporate enhanced user interfaces for improved navigation and readability, along with new filter management features that will allow users to apply and manage filters within individual reports or across multiple campaign reports.
Filter Creation and Application: Alongside improvements to HTML reports, THOR Cloud will enable users to create and manage filters on both a campaign-specific and a global level.
User Management Enhancements: Updates to the user management system are expected to improve administrative control over user roles and access rights.
SIEM Forwarding Management: Currently, THOR Cloud enables the direct transmission of logs from endpoint scans to any accessible SIEM or log management system via SYSLOG/JSON data streams. Building on this capability, future updates will introduce an API-managed SIEM forwarding feature. This enhancement will allow users to configure THOR Cloud to automatically forward events to a cloud-based SIEM of their choice, streamlining the integration and management of SIEM data streams within the THOR Cloud environment.
AI Integration: The integration of AI technologies is planned to introduce event clustering and automated event assessment. These AI-driven features are designed to improve the accuracy and efficiency of the platform’s threat detection processes.
Legacy Operating System Support: To accommodate a broader range of user environments, THOR Cloud will extend its support to older Windows operating systems through THOR Legacy, allowing the platform to cover systems back to Windows XP and Windows 2003.
THOR Thunderstorm Integration: Future integration with THOR Thunderstorm will enable the THOR launcher to function as a sample collector. This feature will facilitate the transmission of samples to a Thunderstorm service hosted in the cloud, enhancing the platform’s analytical capabilities.
In Conclusion
As THOR Cloud continues to evolve, we’re excited to roll out new features that enhance the capabilities and usability of our platform. With upcoming enhancements like advanced SIEM integration and improved HTML reports, we aim to further streamline the security processes for our users.
We are gearing up to offer THOR Cloud to our existing customer base and to those prospects who have already expressed interest. We will continue to accept and welcome further requests for access as we expand our services.
Stay tuned for these updates, and please reach out to our sales team or visit the product page for more information.
For more information, please contact to contact@smartnet.net.vn